This Is All Complete Complete Conspiracy You Have to Know That
"The Internet was made for conspiracy theory: information technology is a conspiracy theory: i thing leads to another, always another link leading you lot deeper into no thing and no place."
(Stewart, 1999, p. xviii).
Conspiracy theories, defined equally allegations that powerful people or organizations are plotting together in secret to achieve sinister ends through deception of the public (Abalakina-Paap et al., 1999; Wood et al., 2012), have long been an important chemical element of popular discourse. With the advent of the Internet, they accept become more visible than always. Although the psychological literature on conspiracy belief has a relatively brusk history, with near of the relevant research having been conducted only within the past twenty years, it has revealed a great deal regarding private differences between those who more often than not believe conspiracy theories (whom we call "conspiracists") and those who prefer conventional explanations (whom we call "conventionalists"). Conspiracy behavior accept been shown to exist positively correlated with mistrust of other people (Goertzel, 1994) and authorities (Swami et al., 2010); feelings of powerlessness and depression self-esteem (Abalakina-Paap et al., 1999); superstition, beliefs in the paranormal, and schizotypy (Darwin et al., 2011); a perceived lack of control (Hamsher et al., 1968; Whitson and Galinsky, 2008); a Machiavellian approach to social interaction (Douglas and Sutton, 2011); and openness to feel (Swami et al., 2010; but see Swami et al., 2011).
At the present fourth dimension, questionnaire-based investigations of individual differences make upwardly the majority of the existing inquiry, although experimental approaches are emerging (due east.g., Douglas and Sutton, 2008; Jolley and Douglas, 2013). A fairly contempo development in the field has been an acknowledgement that in addition to trait-like variables and transient psychological states, ideologies and broad belief systems play a substantial role in conspiracy theory belief. For instance, in an examination of conspiracy theories regarding an alleged cover-upward of the divinity of Mary Magdalene and the bloodline of Christ, Newheiser et al. (2011) demonstrated that the plausibility of these theories hinged largely on broader beliefs about the world. People with traditional Christian behavior were probable to reject such theories out of hand, while those with a more than New Historic period approach were much more receptive. In a like vein, Lewandowsky et al. (2013b) demonstrated that rejection of climate science (though non explicitly conspiracist) is determined in part past ideological concerns, with libertarian complimentary-market ideology, apparently predisposing people to believe that anthropogenic global warming is an unscientific hoax. It is clear, then, that private conspiracy theories or related counter-normative explanations tin seem more or less likely depending on how they comport with other beliefs held by the audience.
Some researchers take gone further, proposing the being of a conspiracist worldview—a conventionalities system conducive to conspiracy beliefs in full general (e.g., Goertzel, 1994; Swami et al., 2010; Wood et al., 2012). This proposal stems primarily from the finding that behavior in unrelated conspiracy theories tend to intercorrelate: for instance, someone who believes that Princess Diana was deliberately assassinated is as well more likely to believe that the moon landing was a hoax. Indeed, Woods et al. (2012) demonstrated that fifty-fifty behavior in directly contradictory conspiracy theories were positively correlated with one another, indicating that conspiracy beliefs may be held together non by direct agreement with ane another, but by mutual agreement with higher-society behavior near the world. One particularly important element of the conspiracist worldview is thought to exist a generalized opposition to official or received narratives. In this view, conspiracy belief is not virtually believing in particular alternative theories, but in disbelieving in whatever the official story is. This tendency has been informally noted past Dean (2002), who described most conspiracy theories as "bits and pieces without a plot… [that] fail to delineate any conspiracy at all. They simply counter conventional narratives with suspicions and allegations that, by and large, resist coherent emplotment" (p. 92). Likewise, Clarke (2007) observed that conspiracy theories are ofttimes extremely vague, particularly in the Internet age.
If this is the instance, then for people who hold a conspiracist worldview, the specifics of a conspiracy theory are less important than its identity equally a conspiracy and its opposition to the official caption. The important element is that those in power are lying and cannot be trusted, and that they are covering up something sinister. Opposition to officialdom, in this sense, parallels the generalized prejudice that Adorno et al. (1950) found to exist stiff plenty to overcome contradictions between unlike anti-Jewish stereotypes. More than being a specific belief that Jews are overly secretive or overly intrusive, anti-Semitism appears to be more of a general belief that Jews are generally unpleasant people. Besides, conspiracy theory belief appears to exist more of a negative belief than a positive one—it is more concerned with saying what the cause of a condition or event was non (i.eastward., whatsoever the official explanation is) than with putting forward a specific alternative account.
An opportunity to test this idea presents itself in the course of observation of online discourse. In spite of, or perhaps considering of, the lack of mainstream public acceptance for their theories, many conspiracists, both prominent and otherwise, appear to meet themselves every bit having a duty to spread their views to the public at big. They oft exhort the unthinking masses to "wake upwards" (east.g., Crane, 2008; Byers, 2009; Icke, 2012). This is a reasonable reaction: given a belief that people's lives are beingness manipulated by malevolent forces beyond their command, near would probably agree that trying to spread the discussion virtually that fact is a skillful idea. Outspoken conventionalists, such every bit those in the "skeptic" movement (east.m., Randi, 1982; Sagan, 1995; Shermer, 1997; Novella, 2009), discover most conspiracy theories to exist misguided at best and destructive at worst, and so brand a point of arguing against them in the public sphere.
This word is voluminous and highly visible in many arenas, perhaps none more so than news website comment sections. Articles about topics for which popular conspiracy theories exist, such as nine/xi, the moon landing, and vaccines, can take tens of thousands of comments, nearly of which are devoted to advancing or refuting allegations of conspiracy. These comments are oftentimes archived forth with the associated articles for months or years afterward, which provides an splendid opportunity for archival research to requite some insight into the thoughts and beliefs of those writing them (e.grand., Fat et al., 2012; Loke, 2012; Sisask et al., 2012).
The present study consists of an examination of a large number of conspiracy theory-related persuasive comments on news stories. Such analysis of online discourse as a method of examining psychological states has increased in prominence as the Internet has become a more pop identify to hash out one'southward ideas. The bailiwick and pace of online give-and-take has been shown to be a more or less reliable barometer of public business concern over social issues (Roberts et al., 2002; Scharkow and Vogelgesang, 2011), and emotional reactions expressed online tin can be used to consistently predict political approval ratings (Gonzalez-Bailon et al., 2012). Quantitative analysis of online discussion has also been used to gain insight into the social psychology of groups with fringe views (Douglas et al., 2005), attitudes toward Tourette's Syndrome (Fat et al., 2012), and racial views (Loke, 2012). Qualitative research on online discourse has been more common, including a report demonstrating the evolution of conspiracy theories over time in response to bear witness (Lewandowsky et al., 2013a). In the context of conspiracy theories in detail, in that location are several advantages to content analysis of online commentary. The self-selective nature of online communication allows for the drove of a groovy deal of information regarding opinions that may be held past only a minority of people; moreover, the degree of anonymity facilitates the honest expression of opinions that might non be held in loftier social esteem elsewhere (east.g., Douglas et al., 2005; Loke, 2012).
At that place are some caveats associated with analyzing persuasive comments in particular. While external validity may benefit from observing behavior in a naturalistic setting, in that location is some caste of doubt regarding the internal validity of any conclusions drawn from such methods. About obviously, there is the event of to what degree the content of persuasive communications reflects the properties of the author rather than the demands of the situation. Rather than faithful representations of internal psychological processes, commenters' methods of argumentation might instead reflect strategic considerations regarding the audience, the venue, and the subject matter. While self-presentation is very often a concern in psychological research, even in laboratory settings, such demands may be peculiarly salient in a state of affairs where one'southward goal is implicitly (or even explicitly) to persuade others rather than to provide an honest and straightforward account of one's beliefs. Indeed, some inquiry has shown that people do accommodate their persuasive techniques according to their noesis of the audience and the subject (Friestad and Wright, 1999; Douglas et al., 2010; Vogel et al., 2010).
The question of whether we can look persuasive communication to accurately reflect inner psychological processes is not hands answerable, as the result of lay persuasive noesis on generation of persuasive arguments is adequately sparse. While there is a substantial body of inquiry on lay persuasive knowledge, the vast majority of it focuses instead on how such knowledge affects susceptibility to the persuasive letters of others. Still, it is well-established that people tend to rely heavily on projection for predicting others' behavior—that is, they utilize themselves as a model for prediction. This upshot is especially strong when relatively piddling is known about the target [for a review, encounter Robbins and Krueger (2005)]. In full general, so, it is likely that persuaders use the self as a model for argument generation: in other words, they argue in a way that they would themselves find convincing. This, in plow, suggests that the types of arguments used by persuaders tin contain data relevant to understanding how they think about the issue at hand.
The trend to use social projection is especially relevant in online settings. Much online give-and-take is either fully bearding or conducted under pseudonyms, profoundly limiting the corporeality of information available nearly the other party in a discussion. Equally such, we assume for the purposes of the present study that people will generally tend to apply arguments that they themselves would notice well-nigh disarming were they the audience rather than the persuader. This, in plow, should reflect the structure of their belief systems—the arguments that people find most convincing are those that lucifer up with how they view the world (Darwin et al., 2011; Newheiser et al., 2011; Wood et al., 2012; Lewandowsky et al., 2013b). To that end, nosotros systematically coded and analyzed conspiracist and conventionalist persuasive comments from iv major news websites on manufactures relating to 9/11 from the menstruation of July 1st through December 31st, 2011, encompassing the months surrounding the tenth anniversary of the attacks.
9/11 conspiracy theories provide an excellent research discipline for several reasons. First, the community associated with these theories, known as the nine/11 Truth Movement, is noted for its substantial online presence and focus on Internet proselytizing. Bartlett and Miller (2011) observed that the movement's "mass membership courage" (p. 45) devotes a substantial corporeality of time to producing large numbers of online comments, and Clarke (2007) saw the Truth Movement every bit a paradigmatic case of Cyberspace conspiracy civilisation. 2d, the timing was fortuitous, with the 10th anniversary of the 9/11 attacks, sure to herald a number of stories on the field of study and therefore many relevant comments, having occurred shortly before information collection commenced. The recency of the materials lowered the probability of comments having been expunged from archives or lost as an unintended consequence of comment software upgrades. Third, just as the Truth Motility has a substantial online presence, then also practice its conventionalist opponents in the skeptic motility. We therefore expected that there would be a good bargain of contend between the two sides, providing farther raw materials for analysis. Finally, the Truth Move is a well-established customs with a substantial intellectual output, including popular books (e.thousand., Griffin, 2004), conference circuits, several sub-organizations such equally Architects and Engineers for 9/eleven Truth, and at least one peer-reviewed periodical, the Journal of nine/11 Studies. At that place is substantial fence within the Truth Movement regarding whether 9/11 was a controlled demolition, a deliberate intelligence failure, or even the consequence of exotic space-based weaponry (Barber, 2008). In short, its trunk of piece of work is varied, voluminous, and well-developed, and should therefore exist able to provide a broad range of unlike arguments for analysis.
If our reasoning regarding the influence of projection on persuasive tactics holds, nosotros should see systematic differences in the characteristics of conspiracist and conventionalist arguments. Specifically, we should exist able to replicate before results demonstrating that unrelated conspiracy beliefs are intercorrelated (e.g., Goertzel, 1994; Swami et al., 2010; Woods et al., 2012)—in this instance, conspiracist comments should contain more than positive (and fewer negative) references to unrelated conspiracy theories compared with conventionalist comments. Examining a long-standing correlate of conspiracy conventionalities, we as well investigated the caste to which comments contained explicit expressions of mistrust, predicting that conspiracist comments would exist more likely to express mistrust of regime or other targets than conventionalist comments (e.k., Wright and Arbuthnot, 1974; Simmons and Parsons, 2005). Further, nosotros examined expressions of powerlessness, and predicted that conspiracist comments would express more than concerns almost power, as feelings of powerlessness accept been shown to correlate reliably with conspiracy theory belief (Abalakina-Paap et al., 1999). Replicating the previously established relationships between conspiracy beliefs, trust, and power would increase confidence in the present written report's methods and help to justify any novel results derived therefrom.
In addition to verifying the utility of this archival arroyo by replicating previous results, we made several novel predictions. Get-go, if we are correct in our contention that much of the conspiracist worldview is based on a generalized rejection of official explanations rather than on positing detail culling narratives, conspiracist comments should focus on refuting conventional explanations more than on presenting or supporting specific conspiracy theories. Therefore, conspiracist comments, relative to conventionalist comments, should exist more than probable to derogate rival explanations and less likely to promote their own. Second, nosotros elected to examine the veracity of the long-held contention that "conspiracy theory" and "conspiracy theorist" bear an intellectual stigma (e.g., Bratich, 2002, 2008; Coady, 2006). If this is truthful, people should be unwilling to apply the term to themselves and should object when others practise then. As such, we predicted that conspiracists would avoid applying the term "conspiracy theory" to their own beliefs (or "conspiracy theorists" to themselves), and would effort to dispute others' usage of the term. While this might seem an obvious prediction—and indeed many authors have it every bit a given that the term is stigmatized—to our knowledge there have not withal been whatsoever empirical investigations of this contention.
Finally, some other possible artery past which the spread of conspiracy theories could be fruitfully understood is social influence theory (Latané, 1981). Since ix/xi conspiracy theories are (at to the lowest degree in the West) an opinion held by a song minority attempting to issue change, social influence theory (Latané, 1981) would predict that conventionalists, if they are skilful majority influencers, are more likely to bear witness patterns consequent with normative social influence. In particular, Bratich (2008) has highlighted the hostility of intellectual orthodoxy toward conspiracist explanations for events and the labelling of conspiracists as paranoid or otherwise mentally ill (c.f. Hofstadter, 1964; Kalichman et al., 2010). At the same fourth dimension, conspiracists are oft hostile in a different style, dismissing conventionalists as naïve, gullible, and either unwitting dupes or willing stooges of the conspiracy (Crane, 2008; Byford, 2011). Therefore, we examined the hostility of each persuasive comment, whether characterized by outright insults, threats, dismissive sarcasm, accusations of complicity, or other hostile or insulting content.
Materials and Methods
Articles
The raw data consisted of the comment sections of various online news articles. Samples were taken from news articles posted betwixt July 1st and December 31st, 2011, on four mainstream news websites: ABC (American Dissemination Company) News, CNN, the Independent, and the Daily Mail. This engagement range was called considering of the large number of 9/11-related manufactures around the time of the tenth anniversary of the attacks, and these four news sites were selected on the reasoning that an ideal sample would not be restricted to a single country, journalistic style, or ideological position, also as for more than applied reasons such as search capabilities, comment archiving, and unpaid access.
Relevant manufactures were selected by searching for a series of terms within the specified date range: "9/eleven," "11/9," "September 11th," "11th September," "globe trade center," "earth trade heart," "wtc," "al-qaeda," "shanksville," and "building 7." Where possible (i.e., the Post and Independent) the websites' own advanced search functions were used; on the remaining sites, we conducted the required searches using Google News.
Comments
For each article that resulted from these searches, the public annotate sections were read, and from these, we extracted verbatim all relevant comments regarding the ix/11 conspiracy theories. Specifically, since only persuasive comments were of interest, only comments containing original content that could be considered persuasive, or written with the intent to persuade, were extracted. Our analyses, for the well-nigh part, are predicated upon the idea that people will tend to project in order to construct persuasive arguments; not-persuasive comments, therefore, are written without regard to their perceived efficacy in convincing the other political party (or neutral parties), as that is not their aim. To operationalize this constraint we adhered to four criteria.
- The comment must not consist solely of insults, ridicule, or threats (e.g., "u stupid sheeple need ii wake upward lol," "Allow me know what your abode address is, and we can have a frank "discussion" nearly your idiotic conspiracy theories"). This criterion was adopted considering insults on their own are not persuasive, and while insults may be relevant to the hostility and stigma variables, they are irrelevant to the bulk of the analyses nosotros wished to comport.
- The comment must non consist solely of "meta" discussion (e.g., "I run across the authorities disinfo automobile is working overtime with all the shills posting here," "can't believe CNN is letting these tinfoil hat nutjobs hijack a story about the 9/11 memorial"). As with insults, "meta" comments do not make persuasive arguments, and are in fact well-nigh entirely different subject affair—they are concerned with the minutia of discussion rather than with the conspiracy theories and conventional explanations in question.
- The comment must not consist solely of a link to an external website, YouTube video, or similar, or a link with minimal description that adds no meaningful content (due east.thousand., "become to ae911truth.org for some informed discussion nearly 9/11," "google Popular Mechanics 9/xi debunking"). While information technology would be in principle possible to lawmaking the contents of such videos, websites, and other bodies of Spider web content, they are ordinarily prohibitively large (particularly in the case of exhortations to carry a Web search for a detail phrase, such as "Building 7," that returns millions of results) and would crave an entirely different fix of coding criteria. Moreover, the linked content was uniformly the work of others rather than the commenter'due south own reasoning, as would be necessary for our reasoning apropos the link betwixt argument generation, projection, and internal psychological representations to concur.
- The annotate must not be copied verbatim from an external source. This was determined by conducting spider web searches when a comment was extremely long, independent unusual formatting such as inappropriate line breaks, or was out of character in terms of word pick or grammatical ability for a previously recognized commenter. Every bit with external links, these passages were not generated by the commenters and the project line of reasoning therefore cannot be assumed to apply in this example as information technology would in the case of original arguments. As such, when an otherwise original post contained a passage quoted from an external source, only the original content was coded.
The author of each comment was recorded, along with the Web address of the parent news article and whether the comment was a direct reply to another, previously posted comment.
Coding
In one case the comments were collected, they were coded co-ordinate to the hypotheses of involvement. The tone of the comment (conspiracist or conventionalist) was of interest to all analyses, so this was the first content variable coded. Conspiracist comments were identified equally whatever that either directly put forrard a conspiratorial account of the events of nine/11, in whole or in part; that challenged the official account in a manner implying conspiracy or complicity amongst governments, intelligence services, corporations, occult associations, or undercover societies; that otherwise favorably referenced common tropes of the 9/11 Truth Motion and its associated trunk of arguments, such every bit cryptic allusions to the fate of Earth Trade Center (WTC) Building vii, popular quotations from conspiracy websites or prominent theorists, and and then on; that responded to conventionalist comments in a manner implying that the original commenter had the incorrect impression in thinking that the attacks were perpetrated by agents of Al-Qaeda; or that was somewhat ambiguous in isolation only was written by a commenter previously observed to make conspiracist arguments or in the context of an argument or point made in the parent article that otherwise made the commenter's intent clear. Therefore, a comment on an article about a new book on ix/eleven reading "Does the volume explain how WTC7 imploded from fire, how a single passport was constitute intact inside hours, how Bin Laden was in the American hospital in Dubai weeks before, how fighter jets were diverted 1000s of miles abroad, how NORAD was ordered to stand up down… " was coded equally conspiracist. While this comment does not directly allege conspiracy, it refers obliquely to many common nine/xi conspiracist arguments and seems conspicuously intended to raise doubt regarding conventional explanations of 9/11.
Conversely, comments were coded as conventionalist if they explicitly endorsed or provided prove in support of the mainstream account of ix/11 or some other unofficial yet non-conspiracist explanation (such as Al-Qaeda independently planting bombs in the Twin Towers or bringing explosives onto the hijacked shipping); if they argued against specific 9/11 conspiracy theories or conspiracist arguments such equally those shown in the sample comment above; or, equally in the case of conspiracist comments, if they were ambiguous in isolation but were written by a previously established conventionalist or in the context of a discussion thread or point made in the parent article that otherwise fabricated articulate the commenter's intent. For instance, the comment "LOL! Wow! What a conspiracy. Man, that tin foil lid has got to exist tight today. Thousands of conspirators would be needed to pull off even a fraction of what you claim. And every one of them has been silent for almost 10 years now. Incredible…" was coded every bit conventionalist due to its argument that the conspiracy explanations of nine/eleven are implausible and general mockery of conspiracists.
Since the first hypothesis concerned the number of unrelated conspiracy theories mentioned favorably and unfavorably in the annotate, we coded two dissever variables for each comment: 1 comprised the number of other conspiracy theories mentioned favorably, and the other comprised the number of other conspiracy theories mentioned unfavorably. Chiefly, these counts did not include "superconspiracies," or conspiracies that orchestrate other conspiracies (Barkun, 2006), of which ix/11 was thought to be a part. For instance, if a commenter defendant the Bilderberg Group or the Illuminati of masterminding the 9/11 attacks, this would be considered part of the ix/11 conspiracy theory rather than a dissever conspiracy theory entirely. However, if the commenter expressed the opinion that the Illuminati orchestrated both 9/11 and the JFK bump-off, the latter would be included as an additional conspiracy theory.
The side by side hypotheses concerned trust and powerlessness. We therefore coded whether each annotate independent expressions of mistrust, whether broadly or narrowly targeted (e.k., "never believe what the media tells yous" or "nobody's trustworthy these days"), as well as powerlessness (e.m., "they've won, there's nothing we tin exercise").
Our chief hypothesis, and the one most relevant to the issue of conspiracist belief systems, concerned whether the comments contained positive or negative arguments. As such we coded for two split binary-valued variables: first, whether the comment contained advocacy of the person'south favored estimation (e.g., "thermite residue in the wreckage is consistent with controlled demolition," "part fires can burn hot enough, uncontrolled, to weaken structural steel to the indicate of plummet"); second, whether the comment contained derogation of the opposing estimation ("there is no way that a airplane would accept left so picayune wreckage at the Pentagon," "it's totally implausible that such a large conspiracy could be kept secret for then long"); and third, whether the annotate directly put forward an caption for either the entirety of 9/11 or an element of it ("ix/11 was an inside job," "the collapse was caused past terrorists flying planes into buildings, cipher more").
We were as well interested in how commenters used the term "conspiracy theory." As such, we created a nominally-coded variable with values representing the unlike ways in which the annotate used the phrase and its variations: non at all; applied to an opposing estimation ("that's just a crazy conspiracy theory"); applied to the commenter's ain interpretation ("it may be a conspiracy theory, only it's yet true"); both; or disputed in its applicability ("calling something a conspiracy theory is but a way of silencing dissent"). This included variations on the term, such every bit "conspiracy theorist," "silly conspiracy nonsense," etc.
The concluding hypothesis concerned the degree to which persuasive conspiracist and conventionalist comments were hostile. Equally such, we coded the hostility of each annotate toward those who hold opposing views on a scale of one (non at all hostile) to five (extremely hostile).
An example of how one mail service was coded on all variables is every bit follows:
"No information technology's you who needs to check his/her facts, Delft Academy burnt from the sixth floor to the top and only a portion of the building on north side collapsed, check out the photos of the building after the fire they're easy to find. They fifty-fifty managed to remove all of the books from the library on the first flooring undamaged after the partial collapse. Nothing about the WTC buildings or Delft University's structures, fires, or collapse/partial collapse are comparable. As far as I tin can tell the WTC buildings are still the merely large steel framed high-rise buildings to suffer total plummet due to fire, your poorly researched comment doesn't disprove the statement anyway."
This annotate, from a Daily Mail article, was part of a lengthy discussion regarding the plausibility of the WTC buildings collapsing due to fires and structural damage, as posited in the conventional explanation. This comment was made in response to a conventionalist who claimed that there is precedent for similar collapses and that the official explanation is therefore plausible. The comment claims that the WTC plummet and the example given by the conventionalist are non comparable, and emphasizes the unique (and therefore suspicious) nature of the WTC collapse. This annotate was therefore coded as derogating rival explanations, only non advocating its own or direct posing a cause of the collapse. It contains no expressions of mistrust or powerlessness, mentions no other conspiracy theories, and does not mention the phrase "conspiracy theory" or any of its derivatives. Nonetheless, it contains some hostility in the first and final sentences, giving information technology a hostility rating of ii.
Data Preparation
While a wide diversity of comments were obtained, certain series commenters tended to dominate the chat across several news articles and even multiple websites. The sample of 2174 comments contained 1156 unique authors, of whom 321 commented more once. Therefore, in improver to analyzing the unabridged collection of comments, nosotros conducted a divide assay in which nosotros calculated the hateful values of each variable for each individual author and repeated the analysis on the level of authors rather than comments. All results obtained below were found at both the author and comment levels of analysis, which provides some assurance that any furnishings found are not the issue of a few prolific commenters skewing the overall distribution of the information. For the sake of brevity, however, only the comment-level analysis is reported beneath.
Inter-Rater Reliability
A random sample of 10% of the comments was coded past a second rater, and reliability analyses were conducted to determine the degree of concordance between the two raters. Cohen'southward kappa (κ) was used for all variables except hostility, the only ordinal variable, for which we instead calculated the intraclass correlation coefficient (ICC). Values of κ from 0.81 to one.00 bespeak almost perfect reliability, while reliability between 0.61 and 0.80 is considered "substantial" and from 0.41 to 0.60 "moderate" (Landis and Koch, 1977). Agreement regarding the conspiracist vs. conventionalist tone of each comment was high, κ = 0.84. Every bit the reliability of the other variables used would depend heavily upon their nomenclature as conspiracist or conventionalist, further reliability analyses were express to those comments on whose tone both raters agreed. Accordingly, advancement of the commenter'southward own explanation (κ = 0.64), derogation of the opposing explanation (κ = 0.61), and the usage of "conspiracy theory" (κ = 0.70) all showed substantial interrater reliability, while mistrust (κ = 0.49) and direct statements of what happened (κ = 0.55) showed moderate reliability (Landis and Koch, 1977). Hostility ratings were besides acceptably reliable, ICC = 0.72. Finally, so few examples of powerlessness were found in the results that it was impossible to describe any conclusions regarding their relative prevalence in conspiracist and conventionalist comments. As such, reliability analyses were non performed on this variable.
Results
Of the 2174 comments collected, 1459 were coded equally conspiracist and 715 as conventionalist. The iv news websites did non contribute as to the sample, with 65 comments in fifteen threads coming from ABC News, 632 in 29 threads from CNN, 1006 in 64 threads from the Daily Mail, and 471 in 27 threads from the Independent. Nonetheless, each site had approximately the same proportions of conspiracist and conventionalist comments—specifically, about twice as many conspiracist comments as conventionalist: for ABC, 21 conventionalist and 44 conspiracist; for CNN, 218 conventionalist and 414 conspiracist; for the Daily Mail, 330 conventionalist and 676 conspiracist; and for the Independent, 146 conventionalist and 325 conspiracist; χ2 (iii) = ane.514, p = 0.68.
Table i shows the general results of the coding analysis. In line with our predictions, conspiracist comments mentioned more non-9/11 conspiracy theories as existence correct than conventionalist comments [1000 = 0.12 per annotate vs. G = 0.02; t (2172) = 3.82, p < 0.001] and fewer such theories as being incorrect [Thou = 0.02 per comment vs. G = 0.18; t (2172) = −seven.51, p < 0.001]. Likewise, conspiracist comments were more probable to express mistrust than their conventionalist counterparts [10.6% vs. 1.iv%; χ2 (1) = 57.22, p < 0.001]. We were unable to test the powerlessness prediction, notwithstanding, equally but two comments in the unabridged sample contained expressions of powerlessness.
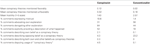
Table 1. Rhetorical components of conspiracist and conventionalist comments.
Assay revealed a number of differences between the rhetorical styles of conspiracist and conventionalist commenters. Thirty-i percent of conspiracist comments contained information that constituted back up for their own position, compared to 56% of conventionalist comments. This deviation was significant, χii (i) = 121.69, p < 0.001. In contrast, 64% of conspiracist comments involved derogation of the opposing explanation, significantly more the 44% of conventionalist comments that did the aforementioned, χ2 (1) = fourscore.13, p < 0.001. Unexpectedly, while only 19% of conventionalist comments direct put frontward an explanation for the events of 9/xi, 52% of conspiracist comments did so, χ2 (1) = 53.56, p < 0.001.
Conventionalist comments (Yard = ii.08, SD = 1.02) were significantly more hostile than conspiracist comments (M = one.44, SD = 0.79), t (2172) = 16.22, p < 0.001 (meet Tabular array ane). Finally, neither conspiracists nor conventionalists were particularly willing to self-use the term "conspiracy theory" or its derivatives: only 31 conspiracist comments referred to their beliefs equally such, while 63 used the term to depict the official story of 9/11, four used it to describe both theories, and 65 disputed others' use of it. Conventionalists were likely to call opposing beliefs conspiracy theories, with 166 doing and then, compared to only a single comment that self-applied the term and another one that contested its applicability. No conventionalist comments chosen both explanations "conspiracy theories."
Give-and-take
The data were generally consistent with our predictions. Conspiracist comments expressed more favorable opinions most unrelated conspiracy theories than conventionalist comments did. This serves as a conceptual replication of previous findings indicating that beliefs in conspiracy theories tend to be correlated: if someone agrees with 9/11 conspiracy theories, they are likewise more likely to agree with other conspiracy theories (eastward.grand., Goertzel, 1994; Swami et al., 2010, 2011; Wood et al., 2012). Further, in accordance with previous work on the role of trust in conspiracy theory beliefs (e.g., Wright and Arbuthnot, 1974; Abalakina-Paap et al., 1999; Simmons and Parsons, 2005), conspiracist comments were more likely to comprise expressions of mistrust than were conventionalist comments. Despite the unexpected impossibility of testing the powerlessness hypothesis, this cluster of results should increase confidence in the validity of the remainder of the nowadays written report's conclusions. The well-established tendencies for conspiracists to be less trusting than average and for conspiracy theory behavior to intercorrelate take manifested themselves in the persuasive communications examined, which suggests that other tendencies may exercise so as well.
Virtually notably, and in accordance with the idea that opposition to officialdom is a major component of the conspiracist conventionalities system, conspiracy advocates showed a tendency to spend much more fourth dimension arguing against the official explanation of 9/11 than advocating an culling. Conspiracy opponents showed the opposite pattern, advocating their own explanation more than they argued confronting the opposing 1. This blueprint of results supports the idea that conspiracy theories take their basis more than in opposition to officialdom than in beliefs in specific culling theories (Dean, 2002; Wood et al., 2012). For the adherents of the 9/11 Truth Movement examined here, the search for truth consists mostly of finding ways in which the official story cannot be true. There is much less of a focus on defending coherent explanations that can better account for the available bear witness. However, conspiracists were more than probable to provide direct explanations for the events of nine/xi than their conventionalist counterparts were—for case, information technology was more common to see a annotate saying "nine/11 was an inside job" or "WTC7 was demolished" than "9/11 was washed by terrorists" or "WTC7 collapsed because of fires and structural harm." This seems like a paradoxical pattern, but conspiracist comments oftentimes simply stated that nine/11 was an inside chore as a sort of slogan without much to back up it. Many other comments took the form "the official story is incommunicable, therefore 9/11 was the outcome of a conspiracy." For instance, ane representative comment from a CNN article read, "Inside Job 9/11! If it was a real terrorist attack U.S. military would have blew up the planes while in the air before they could striking whatsoever population area!" Furthermore, many of the news articles on which the comments appeared featured the official explanation of 9/xi in some detail, significant that it may take been less necessary for conventionalists to summarize the conventional account themselves.
We likewise found that hostility was higher in persuasive arguments made past conventionalists than in those by conspiracists. As ix/11 conspiracism is by and large a minority viewpoint in the West (WorldPublicOpinion.org, 2008), this makes sense: conventionalists, rather than focusing on presenting novel data, instead endeavor to enforce conformity to the majority viewpoint (Latané, 1981). While the inter-rater reliability for hostility was good, there is a hazard that we may not take captured the full spectrum of responses, equally we specifically excluded comments that consisted solely of threats, insults, or ridicule. Equally such, although we cannot say with certainty that conventionalist comments are more than hostile on average than conspiracist comments, we can say with some confidence that this is truthful among comments that also contained some amount of persuasive content.
Finally, the statistics on the usage of the phrase "conspiracy theory" provide an instructive illustration of how the term is viewed. Few people were eager to apply it to their own positions. Conspiracists were more likely to employ it to the conventional narrative, often counterintuitively referring to it every bit "the official conspiracy theory," or to dismiss the term as needlessly loaded and derogatory, consistent with recent scholarly characterizations (Bratich, 2008). Function of the problem is likely to be the vagueness of the term; while nosotros have provided a working definition in the present written report, there is no universal understanding on what exactly constitutes a conspiracy theory (Coady, 2006). Conspicuously, still, the prevalence of counter-argumentation to the apply of the label by others points to some disdain for the term among conspiracists.
At that place are other possible interpretations for some of these results. For example, the observed difference in the usage of other conspiracy theories between conspiracist and conventionalist comments could be seen every bit an result of rhetorical congruence more than of genuine belief. This pattern could naturally arise as the result of an inclination toward arguing past illustration: conspiracists might compare the 9/11 attacks to the JFK assassination, which a majority of Americans believe was the issue of a conspiracy (Goertzel, 1994), in order to make a conspiracy theory seem more plausible. In contrast, conventionalists could compare 9/11 conspiracy theories to more overtly implausible examples, such as the proposed cover-up of the existence of Bigfoot or the idea that Elvis Presley is nevertheless live, in order to make the point that conspiracy theories in general are not to exist taken seriously. Indeed, a post-hoc exam of the data revealed that 23 comments mentioned the JFK assassination conspiracy theory favorably, while only nine mentioned it negatively. The 7/7 bombing conspiracy theories showed a like pattern, with 6 negative mentions to 16 positive. Other theories, such equally those concerning the moon landing (27 negative, 6 positive), Elvis (21 negative, 0 positive), aliens (20 negative, two positive), and David Icke's reptilian shapeshifters (viii negative, 1 positive), showed the opposite design. Not all of these mentions followed the general design evident in the information; some conventionalists said that while another conspiracy theories are truthful, there is no bear witness for a 9/11 conspiracy, and some conspiracists claimed that while nigh conspiracy theories are bogus, in the case of ix/11 the evidence is sufficient to pass up the official story. This form of argument might ultimately be persuasive: people who portray themselves as nominal conventionalists who notwithstanding, find 9/eleven conspiracy theories plausible are substantially portraying themselves as deviant ingroup members. Such people can be very constructive in exerting social influence on the majority (eastward.g., Maass and Clark, 1984).
Ideas of rhetorical congruency and self-presentation call up the issue of whether people'southward persuasive communications are actually an accurate reflection of their own thoughts and ideas rather than a carefully calculated attempt to engage with others' biases and reasoning. The 9/11 Truth Movement is, by and large, a movement of converts—most "Truthers," at some point, became convinced that their previous belief in the official story was incorrect (Kay, 2011). Therefore, in debating with those who hold the positions they previously held, they might repeat the arguments that first caused them to uncertainty the conventional narrative and shaped their subsequent thinking accordingly. On the other hand, the actual content that the discussions centered upon was ofttimes highly technical, and many of the arguments were unlikely to take been generated entirely by the people doing the commenting. While some commenters fabricated intuitive judgments well-nigh the physics of crashing airplanes and collapsing buildings, many others relied on arguments advanced in websites or documentaries devoted to either advancing or debunking 9/11 conspiracy theories. With the amount of data to cull from, however, the arguments commenters chose to put forward may nonetheless reveal useful data about their own decision-making.
While the results of the present report fit with previous work on belief and disbelief in conspiracy theories, some of the novel results found here would benefit from confirmation via other methodological approaches. If conspiracist beliefs are more often than not structured in the way nosotros posit, it should be observable under experimental weather condition—for instance, people with a conspiracist worldview might detect a piece of show to exist more disarming if it is presented as a refutation of the official business relationship of some event rather than as proof of a specific conspiracy theory. Likewise, while we have confirmed that "conspiracy theorist" is not a well-liked term among conspiracists, we have not investigated its bear upon—if the term is used to depict a certain business relationship of an outcome, the negative associations of it might reduce the perceived plausibility of the argument.
In sum, our results are in agreement with predictions derived from prior research. Consistent with much of the existing literature on private differences associated with conspiracy belief, comments that supported 9/xi conspiracy theories were more likely to express mistrust and to refer to other conspiracy theories favorably. Conspiracists were less overtly hostile than their conventionalist counterparts, and did not appreciate existence called conspiracy theorists. Perhaps most importantly, however, the finding that conspiracists spend more time arguing confronting official explanations than for alternative explanations supports the idea that the conspiracy worldview is based more than on atheism than on positive conventionalities. The coherence of the conspiracist conventionalities system is driven by higher-order considerations such as a disbelief in official narratives, rather than positive beliefs in particular culling narratives. This result as well agrees with previous informal observations by conventionalist commentators, who devote a great deal of time to examining and debunking conspiracy theories. One tactic which conventionalists often charge conspiracists of using is "anomaly hunting":
They imagine that if they can notice (broadly defined) anomalies in that information that would point to another phenomenon at work. They and so commit a pair of logical fallacies. First, they confuse unexplained with unexplainable. This leads them to prematurely declare something a true bibelot, without kickoff exhaustively trying to explicate it with conventional means. Second they utilize the statement from ignorance, saying that because we cannot explain an anomaly that ways their specific pet theory must exist true. I don't know what that fuzzy object in the sky is—therefore information technology is an alien spacecraft (Novella, 2009).
The observed trend of conspiracy theory advocates to contend against conventional narratives rather than in favor of particular alternatives closely resembles this description of anomaly hunting, and also parallels Keeley's (1999) observation that conspiracy theories rely heavily on "errant data" rather than on crafting coherent alternative explanations (p. 117). We argue that in fact, anomaly hunting, or a fixation on errant data, is a manifestation of the way conspiracism is structured every bit a worldview. In general, conspiracy belief is not based around specific theories of how events transpire, though these may exist also. Instead, conspiracism is rooted in several higher-order beliefs such as an constant mistrust of dominance, the confidence that nothing is quite as information technology seems, and the conventionalities that well-nigh of what we are told is a lie. Credible anomalies in official accounts seem to back up this, even if they exercise non point to a specific, well-defined culling. For many conspiracists, there are 2 worlds: one existent and (more often than not) unseen, the other a sinister illusion meant to comprehend up the truth; and testify against the latter is prove for the former.
Disharmonize of Interest Statement
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could exist construed as a potential conflict of interest.
Acknowledgments
The authors wish to acknowledge the contribution of Daniel Jolley for his assistance in coding the comment data.
References
Abalakina-Paap, Thousand., Stephan, W. 1000., Craig, T., and Gregory, Westward. 50. (1999). Beliefs in conspiracies. Pol. Psychol. 20, 637–647. doi: x.1111/0162-895X.00160
CrossRef Full Text
Adorno, T. W., Frenkel-Brunswik, E., Levinson, D. J., and Sanford, R. N. (1950). The Authoritarian Personality. Oxford: Harpers.
Barkun, M. (2006). A Culture of Conspiracy: Apocalyptic Visions in Contemporary America. Berkeley, CA: University of California Press.
Bartlett, J., and Miller, C. (2011). A bestiary of the 9/11 truth move: notes from the front end line. Skeptical Inquirer 35, 43–46.
Bratich, J. Z. (2002). "Injections and truth serums: AIDS conspiracy theories and the politics of joint," in Conspiracy Nation: The Politics of Paranoia in Postwar America, ed P. Knight (New York, NY: New York Academy Press), 133–156.
Bratich, J. Z. (2008). Conspiracy Panics: Political Rationality and Popular Culture. New York, NY: State University of New York Press.
Byford, J. (2011). Conspiracy Theories: A Critical Introduction. London: Palgrave Macmillan. doi: 10.1057/9780230349216
CrossRef Full Text
Coady, D. (2006). Conspiracy Theories: The Philosophical Argue. Aldershot: Ashgate Publishing.
Clarke, South. (2007). Conspiracy theories and the Internet: controlled demolition and arrested development. Episteme 4, 167–180
Darwin, H., Neave, North., and Holmes, J. (2011). Belief in conspiracy theories: the role of paranormal conventionalities, paranoid ideation and schizotypy. Pers. Individ. Dif. 50, 1289–1293. doi: 10.1016/j.paid.2011.02.027
CrossRef Total Text
Dean, J. (2002). "If annihilation is possible," in Conspiracy Nation: The Politics of Paranoia in Postwar America, ed P. Knight (New York, NY: New York University Press), 85–106.
Douglas, K. M., McGarty, C., Bliuc, A. M., and Lala, 1000. (2005). Understanding cyberhate: social competition and social inventiveness in online white supremacist groups. Soc. Sci. Comput. Rev. 23, 68–76. doi: x.1177/0894439304271538
CrossRef Full Text
Douglas, 1000. M., Sutton, R. 1000., and Stathi, S. (2010). Why I am less persuaded than you: people's intuitive agreement of the psychology of persuasion. Soc. Influence 5, 133–148. doi: 10.1080/15534511003597423
CrossRef Full Text
Douglas, K. One thousand., and Sutton, R. M. (2008). The hidden impact of conspiracy theories: perceived and actual influence of theories surrounding the decease of Princess Diana. J. Soc. Psychol. 148, 210–222. doi: 10.3200/SOCP.148.2.210-222
Pubmed Abstract | Pubmed Total Text | CrossRef Full Text
Douglas, G. M., and Sutton, R. M. (2011). Does it take ane to know one? endorsement of conspiracy theories is influenced by personal willingness to conspire. Br. J. Soc. Psychol. 50, 544–552. doi: x.1111/j.2044-8309.2010.02018.x
Pubmed Abstruse | Pubmed Full Text | CrossRef Full Text
Friestad, K., and Wright, P. (1999). Everyday persuasion knowledge. Psychol. Marketplace. 16, 185–194.
Goertzel, T. (1994). Belief in conspiracy theories. Polit. Psychol. fifteen, 731–742. doi: 10.2307/3791630
CrossRef Full Text
Gonzalez-Bailon, S., Banchs, R. Eastward., and Kaltenbrunner, A. (2012). Emotions, public stance, and U.S. presidential approval rates: a 5-yr analysis of online political discussions. Hum. Commun. Res. 38, 121–143. doi: ten.1111/j.1468-2958.2011.01423.x
CrossRef Full Text
Griffin, D. R. (2004). The New Pearl Harbor: Disturbing Questions nearly the Bush Assistants and 9/11. Northampton, MA: Olive Branch Printing.
Hamsher, J. H., Geller, J. D., and Rotter, J. B. (1968). Interpersonal trust, internal-external control, and the Warren Committee report. J. Pers. Soc. Psychol. 9, 210–215. doi: 10.1037/h0025900
Pubmed Abstract | Pubmed Full Text | CrossRef Full Text
Jolley, D., and Douglas, K. M. (2013). The social consequences of conspiracism: exposure to conspiracy theories decreases the intention to engage in politics and to reduce ane'south carbon footprint. Br. J. Psychol. doi: 10.1111/bjop.12018. [Epub ahead of print].
CrossRef Total Text
Kalichman, S. C., Eaton, L., and Cherry, C. (2010). "There is no proof that HIV causes AIDS": AIDS denialism behavior amongst people living with HIV/AIDS. J. Behav. Med. 33, 432–440. doi: ten.1007/s10865-010-9275-seven
Pubmed Abstruse | Pubmed Total Text | CrossRef Full Text
Kay, J. (2011). Among the Truthers: A Journey through America's Conspiracist Surreptitious. New York, NY: HarperCollins.
Keeley, B. L. (1999). Of conspiracy theories. J. Philos. 96, 109–126. doi: 10.2307/2564659
CrossRef Full Text
Lewandowsky, S., Cook, J., Oberauer, K., and Marriot, One thousand. (2013a). Recursive fury: conspiracist ideation in the blogosphere in response to enquiry on conspiracist ideation. Front. Psychol. iv:73. doi: 10.3389/fpsyg.2013.00073
Pubmed Abstract | Pubmed Full Text | CrossRef Full Text
Lewandowsky, S., Oberauer, K., and Gignac, G. (2013b). NASA faked the moon landing—therefore (climate) science is a hoax: an beefcake of the motivated rejection of science. Psychol. Sci. five, 622–633. doi: ten.1177/0956797612457686
Pubmed Abstract | Pubmed Total Text | CrossRef Full Text
Loke, J. (2012). Public expressions of private sentiments: unveiling the pulse of racial tolerance through online news readers' comments. Howard J. Commun. 23, 235–252. doi: x.1080/10646175.2012.695643
CrossRef Total Text
Maass, A., and Clark, R. D. (1984). Hidden affect of minorities: xv years of minority influence inquiry. Psychol. Balderdash. 95, 428–450. doi: 10.1037/0033-2909.95.three.428
CrossRef Full Text
Newheiser, A. M., Farias, One thousand., and Tausch, N. (2011). The functional nature of conspiracy behavior: examining the underpinnings of conventionalities in the Da Vinci Code conspiracy. Pers. Individ. Dif. 51, 1007–1011. doi: 10.1016/j.paid.2011.08.011
CrossRef Total Text
Randi, J. (1982). Play a trick on! Psychics, ESP, Unicorns, and Other Delusions. Amherst, NY: Prometheus Books.
Roberts, M., Wanta, W., and Dzwo, T. H. D. (2002). Agenda setting and issue salience online. Commun. Res. 29, 452–465. doi: 10.1177/0093650202029004004
CrossRef Full Text
Sagan, C. (1995). The Demon-haunted World: Science as a Candle in the Dark. New York, NY: Random Business firm.
Scharkow, M., and Vogelgesang, J. (2011). Measuring the public calendar using search engine queries. Int. J. Public Opin. Res. 23, 104–113. doi: 10.1093/ijpor/edq048
CrossRef Full Text
Shermer, M. (1997). Why People Believe Weird Things. New York, NY: Henry Holt and Visitor.
Simmons, W. P., and Parsons, S. (2005). Beliefs in conspiracy theories among African Americans: a comparison of elites and masses. Soc. Sci. Q. 86, 582–598. doi: 10.1111/j.0038-4941.2005.00319.x
CrossRef Full Text
Stewart, K. (1999). "Conspiracy theory's worlds," in Paranoia within Reason: A Casebook on Conspiracy as Explanation, ed G. E. Marcus (Chicago, IL: Academy of Chicago Press), 13–20.
Swami, V., Chamorro-Premuzic, T., and Furnham, A. (2010). Unanswered questions: a preliminary investigation of personality and individual deviation predictors of 9/xi conspiracist behavior. Appl. Cogn. Psychol. 24, 749–761. doi: x.1002/acp.1583
CrossRef Full Text
Swami, 5., Coles, R., Stieger, S., Pietschnig, J., Furnham, A., Rehim, S., et al. (2011). Conspiracist ideation in Britain and Austria: show of a monological belief system and associations between individual psychological differences and real-world and fictitious conspiracy theories. Br. J. Psychol. 102, 443–463. doi: 10.1111/j.2044-8295.2010.02004.10
Pubmed Abstract | Pubmed Full Text | CrossRef Total Text
Vogel, T., Kutzner, F., Fiedler, Chiliad., and Freytag, P. (2010). Exploiting attractiveness in persuasion: senders' implicit theories well-nigh receivers' processing motivation. Pers. Soc. Psychol. Bull. 36, 830–842. doi: 10.1177/0146167210371623
Pubmed Abstruse | Pubmed Full Text | CrossRef Full Text
Forest, 1000. J., Douglas, G. One thousand., and Sutton, R. M. (2012). Dead and live: beliefs in contradictory conspiracy theories. Soc. Psychol. Pers. Sci. 3, 767–773. doi: 10.1177/1948550611434786
CrossRef Total Text
Wright, T. L., and Arbuthnot, J. (1974). Interpersonal trust, political preference, and perception of the Watergate affair. Pers. Soc. Psychol. Bull. 1, 168–170. doi: ten.1177/014616727400100158
CrossRef Full Text
mullinssubbillson.blogspot.com
Source: https://www.frontiersin.org/articles/10.3389/fpsyg.2013.00409/full
0 Response to "This Is All Complete Complete Conspiracy You Have to Know That"
Post a Comment